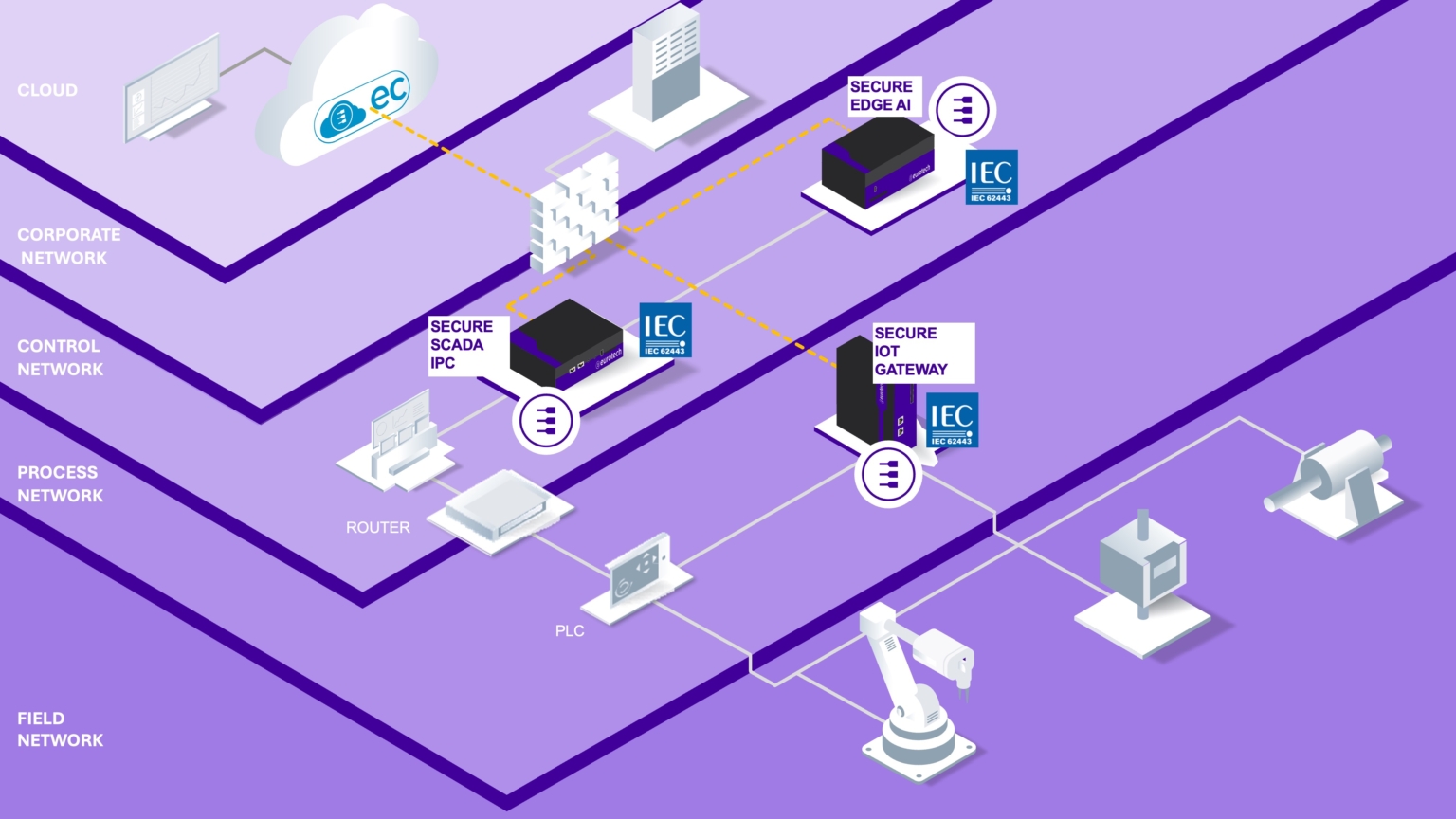
The NIS2 Directive and the Cyber Resilience Act (CRA) are EU regulations aimed at strengthening cybersecurity across the region. NIS2 imposes stricter security and reporting requirements for critical and essential services, while the upcoming CRA sets mandatory cybersecurity standards for products with digital elements, covering their design, development and maintenance. Together, these regulations are designed to protect the EU’s digital infrastructure and systems from rising cyber-attacks.
By selecting a trusted supplier that delivers secure products, companies can start at the component level, ensuring that the first element of the supply chain meets global security standards. Cybersecure computers that comply with the IEC 62443-4-2 (Device Level Security) standard provide a foundational building block for compliance with regulations such as NIS2 and CRA. IEC 62443 is a comprehensive security framework focused on securing industrial automation and control systems (IACS), making it a crucial benchmark for organizations aiming to enhance their cybersecurity posture.